<=Back
Viewed: 1100 times
Share in:



<= KNEC Craft Certificate in ICT module 2 Computer Maintenance and Support past paper: July 2019
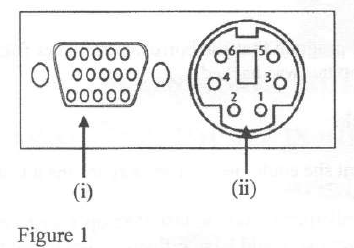
Figure 1 shows ports used in a computer. Identify the port labelled (i) and (ii) stating the I/O devices that connect to each.

Viewed: 1100 times
Share in:



Questions List:
1. Explain the term pixel in computer monitors.
2. Describe platter as used in magnetic disks
3. Differentiate between DIMM and SIMM as used in computer memory.
4. With the aid of examples, Outline two roles of an address bus in a computer.
5. Outline four functions of power supply unit in computers.
6. Explain two reasons for donating old computers to learning institution.
7. Distinguish between solid state memories and magnetic drives in computers.
8. Explain two circumstances under which the main memory of a computer would be replaced.
9. Patricia was required to troubleshoot a computer monitor that was not displaying the graphical user interface after the POST. Outline four possible causes of the problem.
10. Explain two classification of computers according to physical size and processing speed.
11. Davis intends to carry out computer literacy training to his employees. Explain two benefits the company could realize after training.
12. Figure 1 shows ports used in a computer. Identify the port labelled (i) and (ii) stating the I/O devices that connect to each.
13. Paul was advised by his friend to replace a faulty processor for his computer. Explain three possible causes of the problem.
14. List two types of computer keyboard interfaces.
15. Distinguish between Xeon and core-i7 processor as used in computers.
16. Polly was required to adjust the clock of a computer. Outline three methods that she could have used.
17. Ben was called to assist his colleague whose USB mouse for a desktop computer could not have the pointer on the screen. Outline four possible guidelines that he could use to fix the problem.
18. High level formatting for storage disks is normally used by users. Outline four functions played by this type of formatting.
19. Distinguish between safe mode and normal start-up mode as used with computers.
20. Doreen was required to identify different application software used in her computer. List four examples of application software that she could have identified.
21. Outline five safety measures that could be used to protect information stored in computers.
22. Explain three circumstances under which an organization should consider conducting an urgent computer maintenance exercise for its computers.
23. Nelson inserted a flash disk in a computer to print out a stored document but the error message ‘USB not recognized’ appeared on the screen of his computer. (i)Explain the cause of the error message ii)Explain two precautions he need to take with such an error to safeguard his data.
24. Lois installed a computer game that she borrowed from her friend but after one week she noted that her computer was hacked. (i) Identify this type of attack. (ii) Explain two strategies that she could use as a remedy for the attack.
25. Ruth used attended software installation method to install an operating system on her computer. Outline four advantages that could have influenced her to use this method.
26. A motherboard uses firmware on the BIOS chip. (i) Outline three function of this firmware. (ii) Explain two strategies that could be used to maintain performance of the firmware.
27. Alice was required to describe computer troubleshooting method in a job interview. Outline four method that she could have mentioned.
1. Explain the term pixel in computer monitors.
2. Describe platter as used in magnetic disks
3. Differentiate between DIMM and SIMM as used in computer memory.
4. With the aid of examples, Outline two roles of an address bus in a computer.
5. Outline four functions of power supply unit in computers.
6. Explain two reasons for donating old computers to learning institution.
7. Distinguish between solid state memories and magnetic drives in computers.
8. Explain two circumstances under which the main memory of a computer would be replaced.
9. Patricia was required to troubleshoot a computer monitor that was not displaying the graphical user interface after the POST. Outline four possible causes of the problem.
10. Explain two classification of computers according to physical size and processing speed.
11. Davis intends to carry out computer literacy training to his employees. Explain two benefits the company could realize after training.
12. Figure 1 shows ports used in a computer. Identify the port labelled (i) and (ii) stating the I/O devices that connect to each.
13. Paul was advised by his friend to replace a faulty processor for his computer. Explain three possible causes of the problem.
14. List two types of computer keyboard interfaces.
15. Distinguish between Xeon and core-i7 processor as used in computers.
16. Polly was required to adjust the clock of a computer. Outline three methods that she could have used.
17. Ben was called to assist his colleague whose USB mouse for a desktop computer could not have the pointer on the screen. Outline four possible guidelines that he could use to fix the problem.
18. High level formatting for storage disks is normally used by users. Outline four functions played by this type of formatting.
19. Distinguish between safe mode and normal start-up mode as used with computers.
20. Doreen was required to identify different application software used in her computer. List four examples of application software that she could have identified.
21. Outline five safety measures that could be used to protect information stored in computers.
22. Explain three circumstances under which an organization should consider conducting an urgent computer maintenance exercise for its computers.
23. Nelson inserted a flash disk in a computer to print out a stored document but the error message ‘USB not recognized’ appeared on the screen of his computer. (i)Explain the cause of the error message ii)Explain two precautions he need to take with such an error to safeguard his data.
24. Lois installed a computer game that she borrowed from her friend but after one week she noted that her computer was hacked. (i) Identify this type of attack. (ii) Explain two strategies that she could use as a remedy for the attack.
25. Ruth used attended software installation method to install an operating system on her computer. Outline four advantages that could have influenced her to use this method.
26. A motherboard uses firmware on the BIOS chip. (i) Outline three function of this firmware. (ii) Explain two strategies that could be used to maintain performance of the firmware.
27. Alice was required to describe computer troubleshooting method in a job interview. Outline four method that she could have mentioned.