<=Back
Viewed: 815 times
Share in:



<=KNEC Diploma in ICT module I Operating systems past paper: November 2016
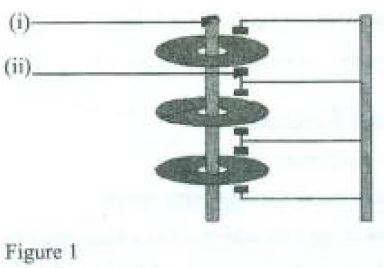
Figure 1 shows a sketch of a section of hard disk. Explain the function of each of the following parts labelled (i) and (ii).
Viewed: 815 times
Share in:



Questions List:
1. Explain the term system call as applied in operating system
2. Outline four benefits of virtual memory in computers
3. Describe three strategies that could be used to mitigate deadlock in operating system
4. Several resources are prerequisite for a successful process execution by the CPU. Outline four examples of these resources that should be availed to the CPU
5. Sifa was required to identify advantages of the pre-emptive job scheduling technique. Explain two advantages that could have identified
6. Outline three file operation that could be applied to a file
7. Define the term sector as applied in computer storage
8. With the aid of a diagram, describe the file allocation table as used in operating system.
9. Outline two limitation of fixed memory partitioning
10. Differentiate between single and double buffering as used in I/O port registers
11. Tom would like to design a memory system that uses best fit placement algorithm. Explain two limitations of this algorithm that would affect the performance of the memory.
12. Explain each of the following terms as used in operating system i)Kernel ii)Monitor
13. Elsie was required to select an operating system that would be used on a server computer to provide a wide range of services to other desktop computers. (i) Identify the most appropriate type of operating system that she could select. Justify your answer ii)Explain two benefits that her computer would realize when using the operating system identified above
14. Explain the term Remote procedure call(RPC) as used in operating systems
15. Differentiate between communication and storage I/O devices
16. A computer is made up of different types of internal buses to facilitate communication Explain two types of such buses found in a computers system
17. Outline three examples of roles that could be provided by a parent process
18. With an aid of a diagram, describe the burst DMA mode of operation
19. With an aid of a diagram, describe the hierarchical file system
20. Deadlocks are inevitable in operating system. Explain two conditions that should hold to trigger this anomaly
21. Name two ways of creating processes during execution by operating system
22. Outline four advantages of peer-to-peer file sharing
23. Differentiate between seek time and rotational delay as used in disk management
24. Identify the type of memory used in each case (i) temporally store results of processing by CPU ii)retains stored information events after computer restarts; (iii)Portion of hard disk that is logically addressed as main memory; (iv)Bridges the speed gap between the processor and RAM
25. Sam was required to enumerate objectives of inter-process in operating system during a regional symposium for programmers. Explain three objectives that he could have outlined
26. Explain the term frame as used in memory management
27. Differentiate between base register and bound registers as applied in memory management
28. Monolithic operating system are not popular. Outline four limitations of monolithic operating that could be influencing this trend
29. With aid of sketches, explain two issues associated with memory fragmentation
30. Maria intend to use round robin job scheduling algorithm in an operating system. Explain three benefits of using this algorithm.
31. Outline two factors to be considered when selecting computer memory, other than cost.
32. Differentiate between I/O bound and CPU bound jobs
33. Define the term dispatcher as used in operating system
34. Describe three advantages of paging memory as used in memory management
35. Figure 1 shows a sketch of a section of hard disk. Explain the function of each of the following parts labelled (i) and (ii).
36. Dennis investigated challenges faced while using non-preemptive job scheduling in operating system. Explain two challenges that he could have established
37. Bernard intends to configure access control list (ACL) in one of his clients file system. Explain two reasons that could influence his decisions
38. Cindy was required to identify characteristics of a 4th generation operating system during an exam. Outline four characteristics that she could have listed
39. RDS company LTD intends to deploy Redundant Array of Independent Disks in its file systems. Explain two benefits that the company could realize from using the technology.
1. Explain the term system call as applied in operating system
2. Outline four benefits of virtual memory in computers
3. Describe three strategies that could be used to mitigate deadlock in operating system
4. Several resources are prerequisite for a successful process execution by the CPU. Outline four examples of these resources that should be availed to the CPU
5. Sifa was required to identify advantages of the pre-emptive job scheduling technique. Explain two advantages that could have identified
6. Outline three file operation that could be applied to a file
7. Define the term sector as applied in computer storage
8. With the aid of a diagram, describe the file allocation table as used in operating system.
9. Outline two limitation of fixed memory partitioning
10. Differentiate between single and double buffering as used in I/O port registers
11. Tom would like to design a memory system that uses best fit placement algorithm. Explain two limitations of this algorithm that would affect the performance of the memory.
12. Explain each of the following terms as used in operating system i)Kernel ii)Monitor
13. Elsie was required to select an operating system that would be used on a server computer to provide a wide range of services to other desktop computers. (i) Identify the most appropriate type of operating system that she could select. Justify your answer ii)Explain two benefits that her computer would realize when using the operating system identified above
14. Explain the term Remote procedure call(RPC) as used in operating systems
15. Differentiate between communication and storage I/O devices
16. A computer is made up of different types of internal buses to facilitate communication Explain two types of such buses found in a computers system
17. Outline three examples of roles that could be provided by a parent process
18. With an aid of a diagram, describe the burst DMA mode of operation
19. With an aid of a diagram, describe the hierarchical file system
20. Deadlocks are inevitable in operating system. Explain two conditions that should hold to trigger this anomaly
21. Name two ways of creating processes during execution by operating system
22. Outline four advantages of peer-to-peer file sharing
23. Differentiate between seek time and rotational delay as used in disk management
24. Identify the type of memory used in each case (i) temporally store results of processing by CPU ii)retains stored information events after computer restarts; (iii)Portion of hard disk that is logically addressed as main memory; (iv)Bridges the speed gap between the processor and RAM
25. Sam was required to enumerate objectives of inter-process in operating system during a regional symposium for programmers. Explain three objectives that he could have outlined
26. Explain the term frame as used in memory management
27. Differentiate between base register and bound registers as applied in memory management
28. Monolithic operating system are not popular. Outline four limitations of monolithic operating that could be influencing this trend
29. With aid of sketches, explain two issues associated with memory fragmentation
30. Maria intend to use round robin job scheduling algorithm in an operating system. Explain three benefits of using this algorithm.
31. Outline two factors to be considered when selecting computer memory, other than cost.
32. Differentiate between I/O bound and CPU bound jobs
33. Define the term dispatcher as used in operating system
34. Describe three advantages of paging memory as used in memory management
35. Figure 1 shows a sketch of a section of hard disk. Explain the function of each of the following parts labelled (i) and (ii).
36. Dennis investigated challenges faced while using non-preemptive job scheduling in operating system. Explain two challenges that he could have established
37. Bernard intends to configure access control list (ACL) in one of his clients file system. Explain two reasons that could influence his decisions
38. Cindy was required to identify characteristics of a 4th generation operating system during an exam. Outline four characteristics that she could have listed
39. RDS company LTD intends to deploy Redundant Array of Independent Disks in its file systems. Explain two benefits that the company could realize from using the technology.